Configuring SELinux for AlmaLinux Security
Secure AlmaLinux with ease! Learn how to set up SELinux for stronger protection. Simple steps, powerful defense. Your system, your safety. 🚀🔒 #AlmaLinux #SELinux #Security

Security-Enhanced Linux (SELinux) is a mandatory access control (MAC) security mechanism implemented in the Linux kernel. It adds an extra layer of security by enforcing access control policies and restricting the actions of processes and users, enhancing the overall security posture of your system. In this guide, we will walk you through the process of configuring SELinux on AlmaLinux to bolster your system's security.
Prerequisites:
Ensure you are logged in as the root user or a user with sudo privileges.
SELinux should be installed by default on AlmaLinux, but if not, you can install it using:
sudo dnf install selinux-policy selinux-policy-targeted -y
Checking SELinux Status
Begin by checking the current status of SELinux on your AlmaLinux system:
sestatusThe output will provide information about whether SELinux is enabled or disabled.

Setting SELinux Modes
SELinux operates in three modes: Enforcing, Permissive, and Disabled.
- Enforcing: Policies are enforced, and violations are logged.
- Permissive: Policies are not enforced, but violations are logged.
- Disabled: SELinux is completely turned off.
To set SELinux to Enforcing mode:
sudo setenforce 1
To set SELinux to Permissive mode:
sudo setenforce 0
Configuring SELinux Policies
SELinux policies are the cornerstone of the Security-Enhanced Linux framework, defining rules and constraints to regulate the behavior of processes and users on the system. While the specific configuration files may vary based on the distribution and version, on AlmaLinux, SELinux policies are typically managed through the semanage tool.
Viewing SELinux File Contexts:
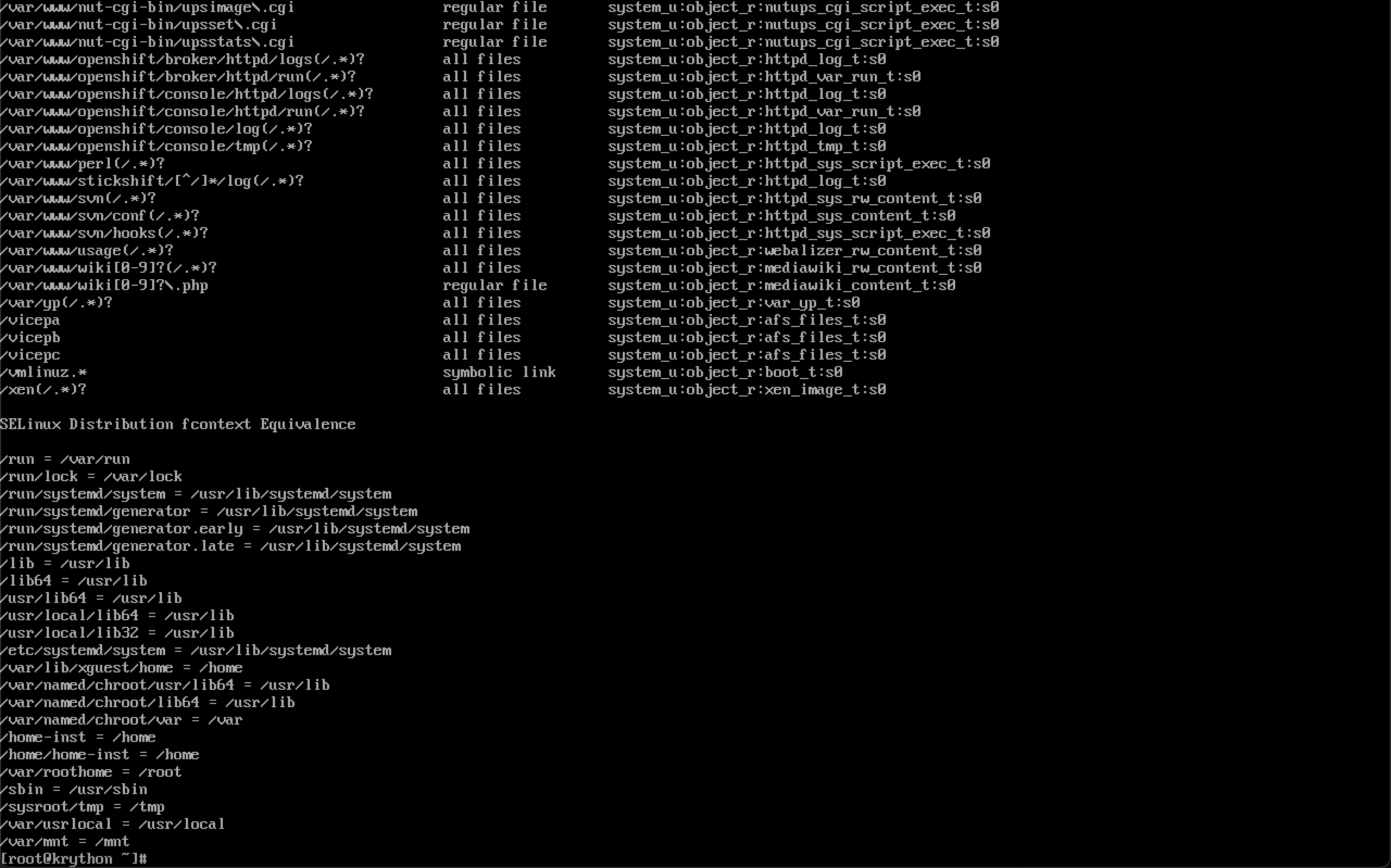
To gain insights into the current SELinux file context mappings for the targeted policy, use the following command:
semanage fcontext -lThis command displays a list of file context mappings, providing information about the relationships between file patterns and their corresponding security contexts.
Customizing SELinux File Contexts:
File contexts play a crucial role in determining how processes interact with files. You can customize file contexts using the semanage tool. For instance, to add a custom file context mapping:
semanage fcontext -a -t httpd_sys_content_t '/path/to/custom(/.*)?'This example associates the httpd_sys_content_t context with files located under /path/to/custom and its subdirectories.
Reviewing SELinux Policy Modules:
SELinux policy modules encapsulate rules that define the access permissions for various processes and objects. To list the currently loaded policy modules:
semodule -lThis command provides an overview of the active policy modules on your system.
Adding Custom SELinux Policy Modules:
If your system requires additional policies, you can create custom policy modules. Use the semodule tool to install a custom policy module:
semodule -i my_custom_module.ppReplace my_custom_module.pp with the actual name of your custom policy module file.
Managing SELinux Booleans
SELinux Booleans are variables that can be toggled to enable or disable specific functionalities within the policy. To view available Booleans and their statuses:
getsebool -a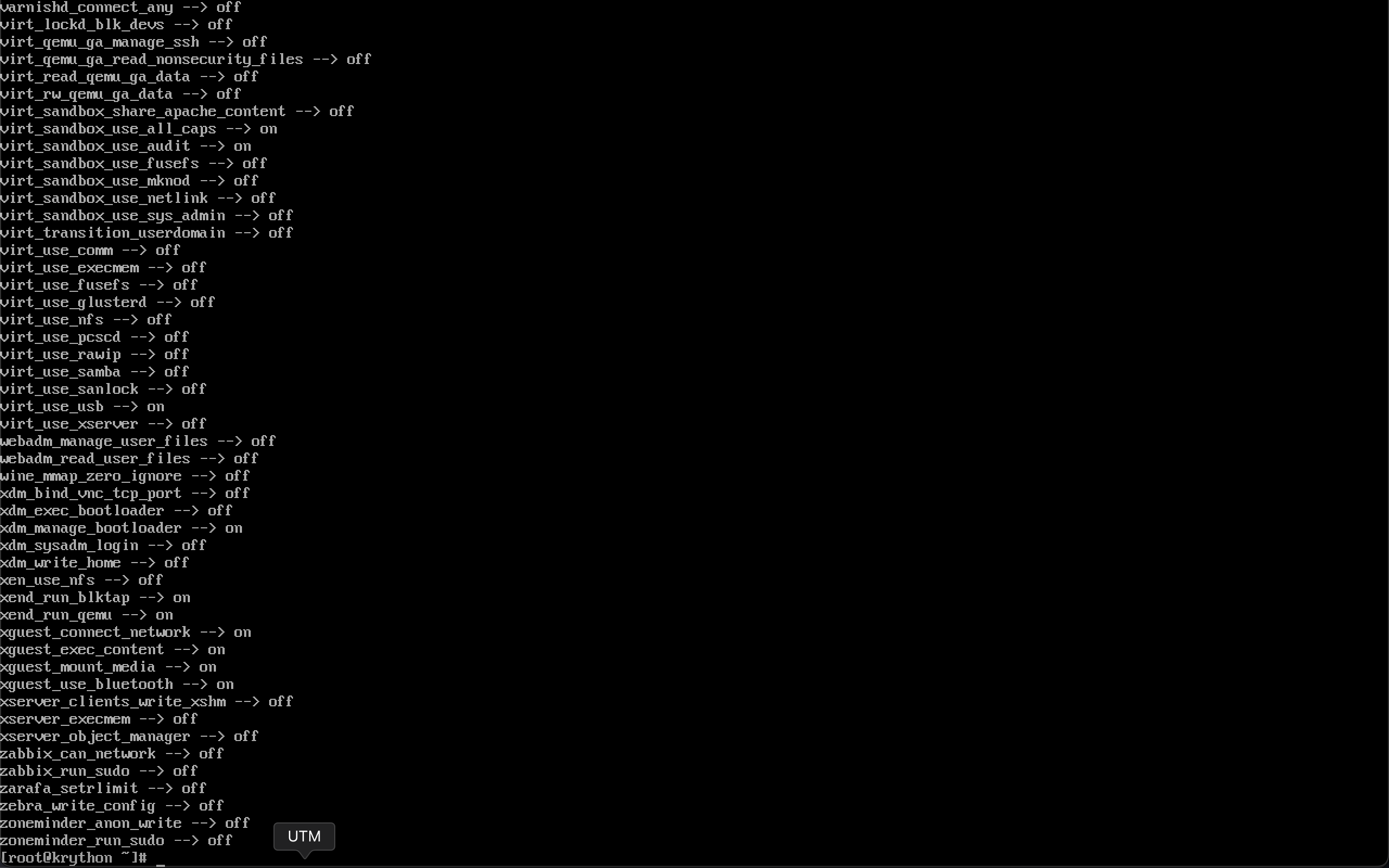
To enable a Boolean (e.g., httpd_can_network_connect):
sudo setsebool -P httpd_can_network_connect on
httpd_can_network_connectTo disable a Boolean (e.g., httpd_can_network_connect):
sudo setsebool -P httpd_can_network_connect off
httpd_can_network_connectTroubleshooting SELinux
If issues arise, check the audit logs for valuable information:
sudo ausearch -m avcAnalyze log entries to identify and address policy violations.
Disabling SELinux
While generally not recommended, temporarily disable SELinux if needed:
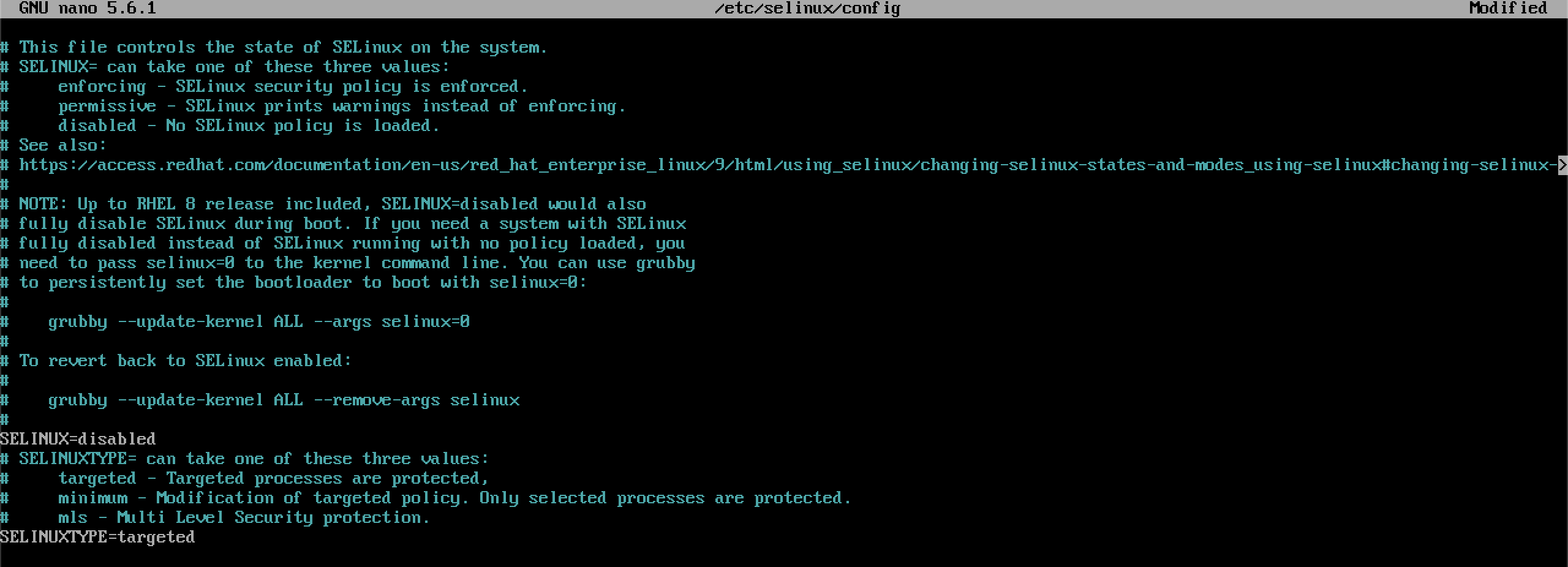
sudo setenforce 0For persistent changes, edit /etc/selinux/config:
sudo nano /etc/selinux/configSet SELINUX=disabled.

Conclusion
You've successfully configured SELinux on your AlmaLinux system, enhancing its security posture. Regularly review and update SELinux policies to align with evolving security needs.
If you encounter challenges or have questions, feel free to leave a comment below. Your system's security is our top priority!